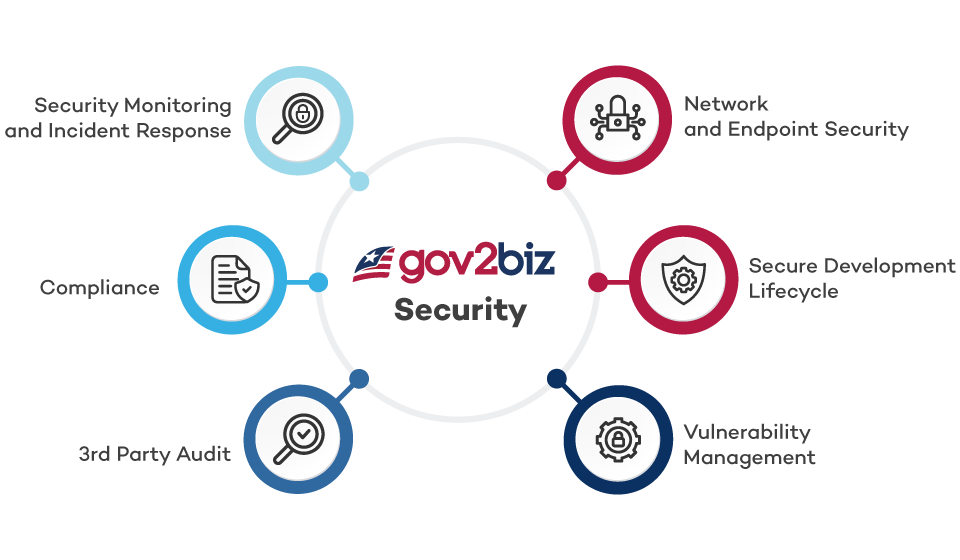
At Gov2Biz Inc, we prioritize security at every level. Our SaaS platform, Gov2Biz, is built on robust security principles to meet the stringent demands of government licensing and regulatory agencies. We understand that our customers manage sensitive data, and our commitment is to provide an ultra-secure environment for that data. This article discusses some of the key aspects of our data and network security strategy. The article is non-comprehensive by design.
Gov2Biz production instances are hosted on AWS GovCloud to provide the highest level of assurance to our customers. AWS GovCloud follows a shared responsibility model as it pertains to security. Under this model, AWS takes responsibility for the security “of” the cloud, encompassing the infrastructure, data centers, and network architecture. This includes implementing physical safeguards, network protection, robust data encryption measures as well as robust physical access controls to its data centers. Gov2Biz is accountable for the security “in” the cloud. This collaborative model is a comprehensive approach to safeguarding sensitive information and maintaining a secure computing environment.
For more information about AWS GovCloud’s infrastructure security in place, please visit https://aws.amazon.com/govcloud-us
Encryption at Rest
To protect sensitive data stored within the Gov2Biz platform, we employ advanced database-level encryption techniques. Our databases are encrypted using industry-standard 256-bit AES encryption algorithms, ensuring that data is secure even in the highly unlikely event that unauthorized access occurs.
Encryption in Transit
Data protection remains paramount while data is in transit. Gov2Biz leverages HTTPS and SSL-256-AES encryption techniques to secure data communications between our platform and end users. This ensures that all data, whether in transit or at rest, remains secure and private, and protected from interception or tampering by unauthorized parties.
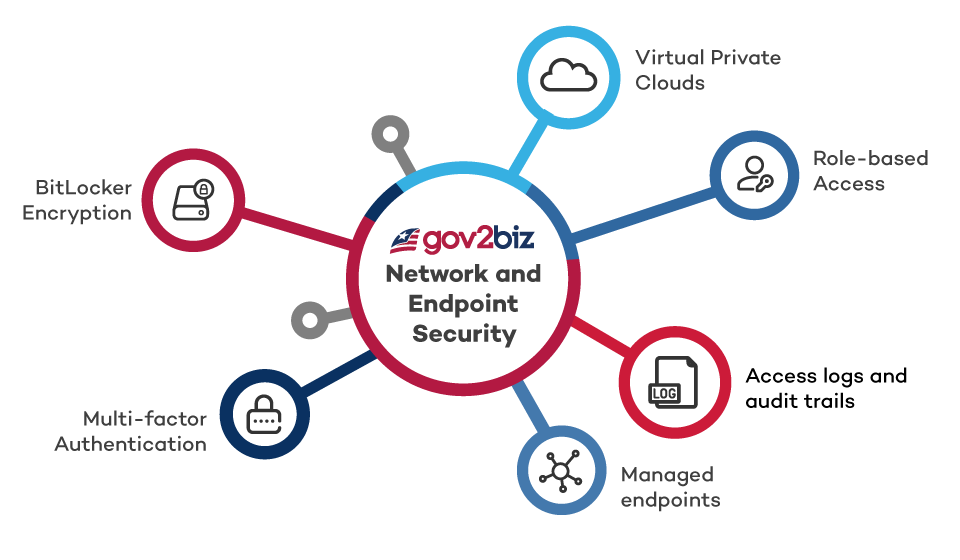
Network Segregation
Our SaaS platform is designed with network isolation as a core principle. Gov2Biz uses Virtual Private Clouds (VPCs) and bastions to provide controlled and monitored access to systems’ backends. This means we can maintain a strong security posture by segregating our network and restricting access to sensitive areas. Access logs and audit trails provide additional transparency and accountability.
Endpoint Security
Access to our systems is tightly controlled. We use multi-factor authentication (MFA), federated access, and strict separation of duties to ensure that only authorized individuals have access to sensitive systems. Additionally, the equipment used to access our systems is hardened, utilizing BitLocker encryption and managed endpoints that are continuously monitored.
Our commitment to security extends to the development process. We integrate security measures into every stage of the software development lifecycle, using a combination of SAST, DAST, Code analysis toolsets, monitors, manual reviews, process controls and training, we are able to build it right the first time, rather than fix it later. This approach allows us to deliver a product that is not just feature-rich, but also secure and reliable.
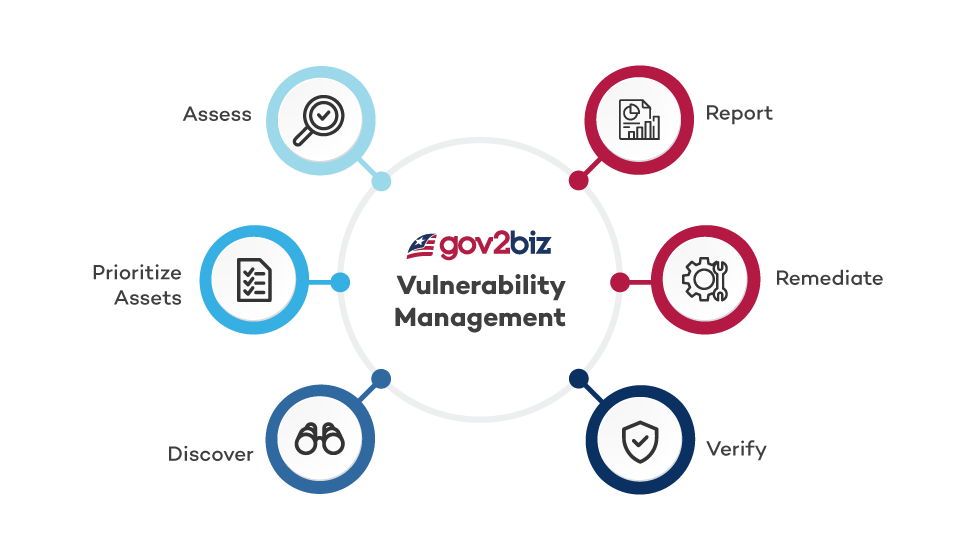
At Gov2Biz Inc., we take a proactive approach to vulnerability management. Our Responsible Disclosure process encourages security researchers to report vulnerabilities in our platform, allowing us to address potential risks before they can be exploited. In addition, our production instances are hosted on AWS GovCloud, which offers enhanced security and compliance features. This involves using Dynamic Application Security Testing (DAST) tools within our development lifecycle to identify potential risks. Additionally, we engage third-party auditors to perform penetration tests, ensuring a robust and thorough review of our systems. This comprehensive vulnerability management strategy enables us to identify, prioritize, and rectify any potential security issues.
Continuous monitoring
Continuous security monitoring is a cornerstone of our security strategy. We employ network security monitoring tools to maintain visibility into system activities and potential threats. This includes IP and geographical whitelisting, ensuring only authorized locations and users can access our systems. Furthermore, automatic compliance monitoring and third-party audit oversight enhance our ability to maintain high security and compliance standards.
Incident Response
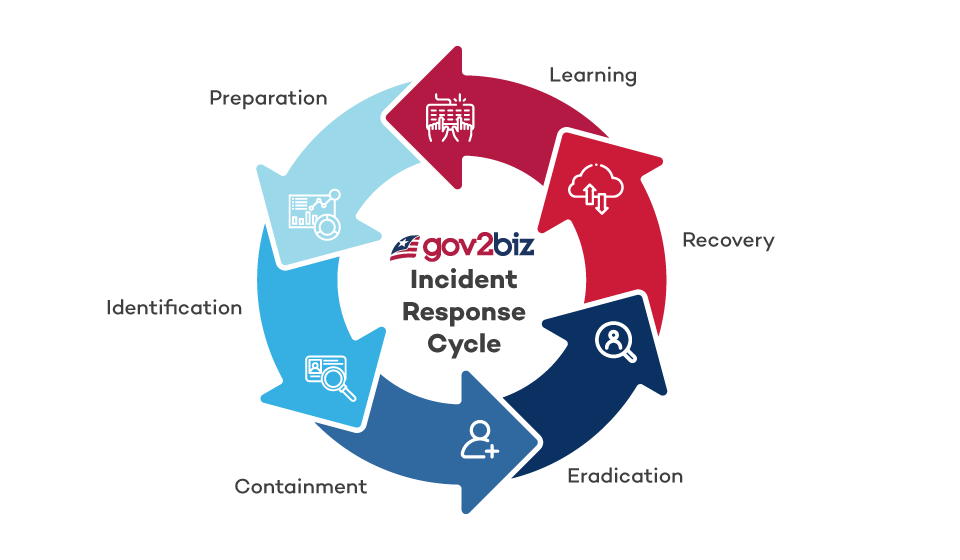
In the unlikely event of a security incident, Gov2Biz has a robust response strategy in place. Our incident response team is trained to act quickly to identify, contain, and remediate any potential threats. This quick action, paired with our rigorous logging and audit trail systems, enables us to effectively mitigate potential risks and prevent further breaches.
Compliance is crucial in the government sector, and Gov2Biz takes this very seriously. We host our production instances on AWS GovCloud, which meets the highest government compliance standards. Furthermore, we engage AWS Compliance monitors and third-party auditors to ensure that we consistently meet and exceed these standards.
In conclusion, at Gov2Biz Inc., we believe that security is not a one-time effort but a continuous process. We are committed to providing a secure environment for our customers by integrating industry-leading practices in encryption, network segregation, vulnerability management and security.